Unknown Borders hit by Ransomware
As part of my daily routine, I start each day by logging on to the main UB server to check up on logs and activities, but instead of seeing the dull grey default background of Windows Server, I were met by a black ominuos screen with the wording "All your important files are encrypted", a chill ran down my back. Frozen in time I simply just kept starring at those torn letters, first unbelieving then followed by panic. I quickly dived into our database folder only to see that every file had suddenly gained a new ending - ".wtf". Looking through several folders I started to realise that indeed, everything had been encrypted. I will admit, I even tried to just change the filetype to whatever they were supposed to be, like some script-kiddy first out of kindergarten, but of course, the files stayed the same. They were encrypted. Finally I understood, we had been hit.
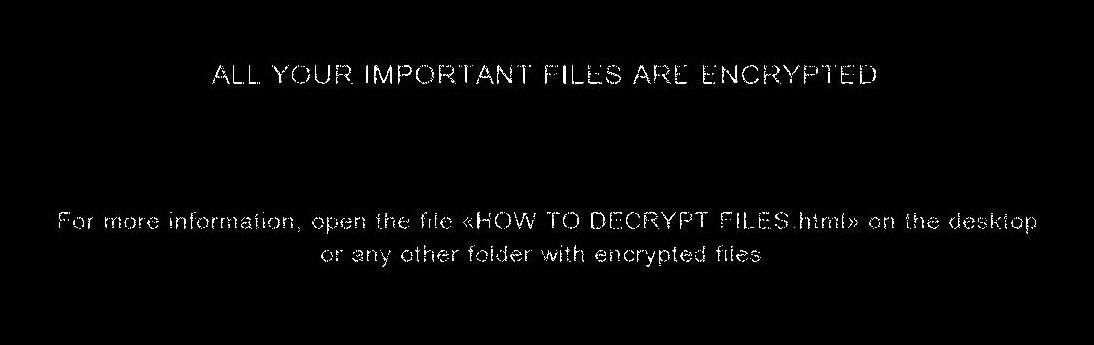
Before I began investigating, I needed to make sure that we were not still under attack. With haste I went into the server room and unplugged the ethernet cable from its socket, and then I simply just stood there. From past experience with these types of attacks I knew that I couldn't simply shutdown the computer, for there might still be remnants left of the virus and it could be hiding anywhere. If I could find the virus, somebody might be able to reverse-engineer it. I then spent several hours scouring threw all the files, looking for any remnants or files that seemed out of place. Every folder was flipped upside down, but to no avail. I was dealing with a virus that had deleted itself after delivering its payload. Leaning back in my chair, I began to formulate a strategy. First I had to warn everybody, then seek professional council, and perhaps then I could find a way around this.
Using the reputable site ID Ransomware, I learned that I were dealing with the Cry36 variant from the CryptON family. With this information I set out to warn all of our users, partners and affiliates. I went on twitter warning all of our followers and networks. Then on the 25th, discord as without any of our sites online, discord would be the place where I could warn people, it also became our outlet during this ordeal.
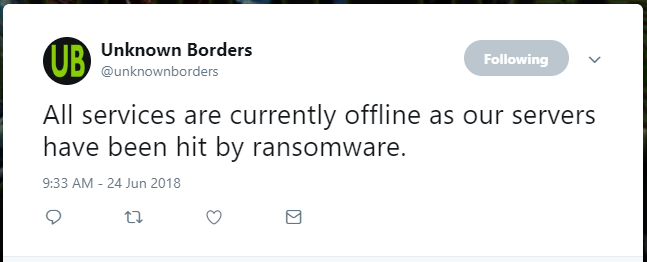
"In total we have 800gb of data that have been encrypted. This includes Databases, Backups, Project Files and some personal files."
Yilmas - Discord, June 25, 2018
Once the news broke that we had been hit, some left out of fear for the dark underworld of hackers. Others chose to stay and support our battle against the unjustified attack that had wrecked the community - their home on the wild and ravenous ocean that we call the internet.
I contacted a high-profile Data Forensic Recovery company here in Denmark, to seek advise. But I soon realised, that not even they could help. The Cry36 was an ingenious variant. There had been no vulnerabilites or flaws located in its code. Only troubling news. It works by encrypting the victims files with an RSA-2048bit encryption, otherwise known as a "military-grade encryption", using an AES-128bit key. In laymans terms, this meant that without the private key which the perpetrator was the sole keeper of, any attempts at decrypting the files without the key would be futile. This was heartbreaking news.
We were left with two options if we wanted to get our data back. Either we wait for the law enforcement of the respective country to crack down on the perpetrator which could take years, or we pay. Professional respect, stubborness and even my pride would prevent me from ever paying the perpetrator.
... we have backups!
At the moment the virus wrecked havoc in our systems, our backup drive was connected to the server as it was performing the weekly backup. Which meant the backup was encrypted as well. But, out of no where came a group of our customers with their own backups. Finally, some good news! Over the evening and late hours of monday way into tuesday, we went at work. I had gathered every eligible affiliate and put them to work on restoring as much as we could. And by 4am on June 26th we had succeded in bringing back 20 sites and 37 databases. This was every single client site and database. We could finally breath a little easier.
Our client sites were indeed online and running smoothly, with barely any data loss. But all of the core UB Network sites were still offline. Their databases had no backups that had been left untouched by the virus. But this recovery operation had given us the spirit to continue. We would not be brought down by those that sought to destroy us.
Pride
A day went by, then two. All of the security outlets had nothing to offer. Even the well known security site of Bleeping Computers, had nothing but strong support and well wishes to offer. Then on June 28th, I swallowed my pride. Loosing 11 years of hard work, setting us back to the point of when I first had the idea of making this community, was something I could not accept. The setback would slowly eat away at my resolve to continue, if I did nothing.
I initiated contact with the perpetrator.
At first I was angry, paranoid, and lost. But, I was surprised to find an almost respectable person at the other end. There were no attempts at misguiding, scamming, or in any other way cause more disruption. And he even agreed to perform a single file decryption - so as to prove that he did indeed possess a decryptor for our files. After verifying that the file had indeed been decrypted and no damage had been caused to the file in the process, I initiated the transfer of bitcoins he had requested. And then I waited. Minutes went by, then an hour, still no response. My mind was every where, did he leave, was this all actually a scam. Then, when I had almost given up hope, I received a mail containing both the private key and the decryptor.
I quickly set out to test this decryptor, first on a singular file. Then a couple more. And finally, I simply let it loose on the old server. I knew, that if anything went wrong, I still had a backup of all the encrypted files. Call me paranoid, but even a backup of encrypted files, are still a backup.
Knowing that we had 800gb of encrypted files, I assumed the decryption process would take hours, if not days. So I was both pleasently surprised and a bit sceptic when only two hours went by before the decryptor was done. Cautiously I started looking through the files, discovering that if nothing else, the file ending ".wtf" had been removed. Holding my breath as I opened one of the files, waiting, and then it was there. As if nothing had ever occured, all the data was there. But we were not home yet, quickly I pulled out another drive and began a backup process of all the now decrypted files. Once that was done, I restarted the server, so that even all the windows services could properly start. Now it was time to inspect the damage.
Every file was intact.
The Aftermath
![]()
Today, July 1st, I can finally say that we have brought back both the community and the company from the brinck of stagnation. We are still missing our main site, but that has nothing to do with data loss or missing files. Instead, we have decided to wait. In the last few months, we have been hard at work redesigning not just our site but also the identity and mission of Unknown Borders. All of which was set to culminate in the reveal of the new site during this summer. So instead of dividing out attention between the old site, and the new. We have decided to focus our attention on the new one. I am writing this article now, so as to keep the article true to the events. So as not to be jumpled up by fractored memories. And when you are reading this, you will be reading it on the new site.
As a company we have learned a hard and expensive lesson, in the matters of security and backups. Therefor we have moved every site that is part of or affiliated with UB Network to Microsoft Azure, and tripled our security layers. Rackspace combined with Azure will take care of our backups. So that now, they will exist in the cloud, and will be bulletproof against such an attack again.
Our physical server will now only handle our game servers and other similar applications. Meaning, if such an attack should occur again, the damage would be minimal. Even the backups of these servers, will be hosted by either Microsoft Azure or Rackspace.This ofcourse comes with a price, but it is one that is neccesary so as to avoid any future attacks.
As a community, this event has only strengthened us. The support that you have given us, has been greatly appreciated. It is that support that has kept us going. I hope, that we can continue to serve all of you to the best of our abilities and provide you with a safe and enjoyable place to belong - A home on the internet.
Finally, let me end this article with a quote by the Chief of NC3, the danish police cyber division, on the matter of ransomware.
"We strongly advise against paying these criminals, but it is not our data..."